Safari's WebKit rendering engine has a flaw that could crash the browser and enable malicious code execution, and Apple hasn't yet patched it even though a fix's been available for weeks.
WebKit
WebKit code references Apple’s unreleased iOS 15 and macOS 12 software updates

Apple's refreshed code for the WebKit layout engine used by Safari and other web browsers includes references to the major iOS 15 and macOS 12 software updates launching this fall.
How to view the website Privacy Report in Safari
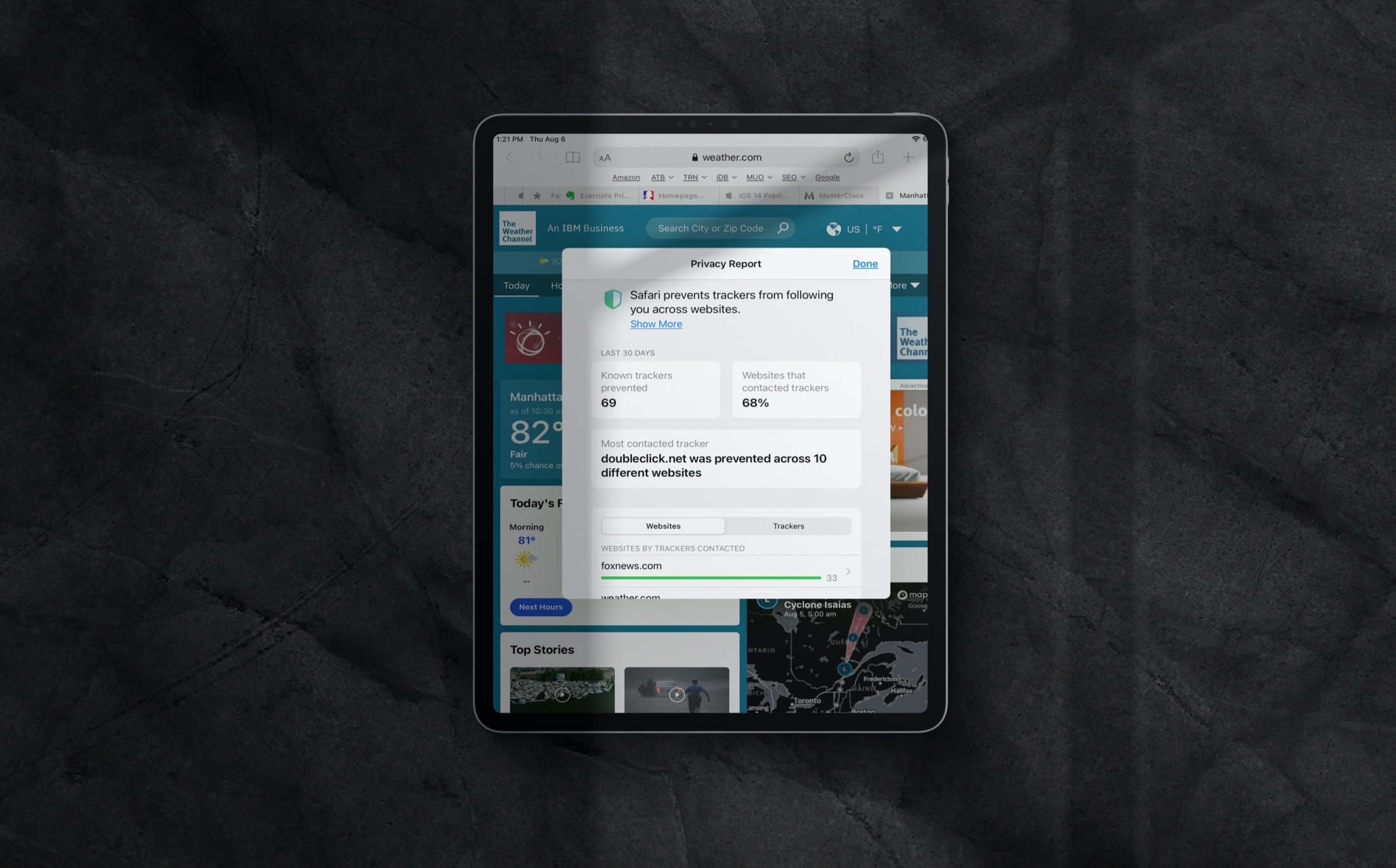
Learn how to review the Privacy Report in Safari on iPhone, iPad, and Mac to see which websites track your activity while you browse.
Luca Todesco has released a WebKit RCE exploit that works on iOS 12.1.4 and earlier

Before the days of Electra and unc0ver dawned upon us, there was Yalu, an iOS 10-centric jailbreak too by the talented hacker Luca Todesco (@qwertoruiopz); but apart from a few teasers here and there, the jailbreak community hasn’t heard much him since the Yalu days – that is, until now.
In a bombshell Tweet shared this week, Todesco released what appears to be a WebKit-based exploit that allows remote code execution (RCE) in web browsers with JIT. What’s more is that the exploit was only just fixed three days ago, which means it should be viable on all versions of iOS up to Apple’s latest release – 12.1.4:
Linus Henze releases Safari-centric exploit targeting iOS 12.1 and earlier

It was only a few days ago that we learned about a sandbox escape PoC for iOS 12.0-12.0.1, and while it was just a proof of concept, there’s always the potential that a talented hacker could make use of it for future endeavors; perhaps even jailbreak development.
Fortunately, that’s not the only iOS 12-centric vulnerability floating around in the wild these days. As it would seem, a Safari-based exploit targeting iOS 12.1 and below (and macOS 10.14.1 and below) was also released this week by iOS tinkerer Linus Henze.
What Progressive Web Apps are and how to install and use them on iPhone and iPad
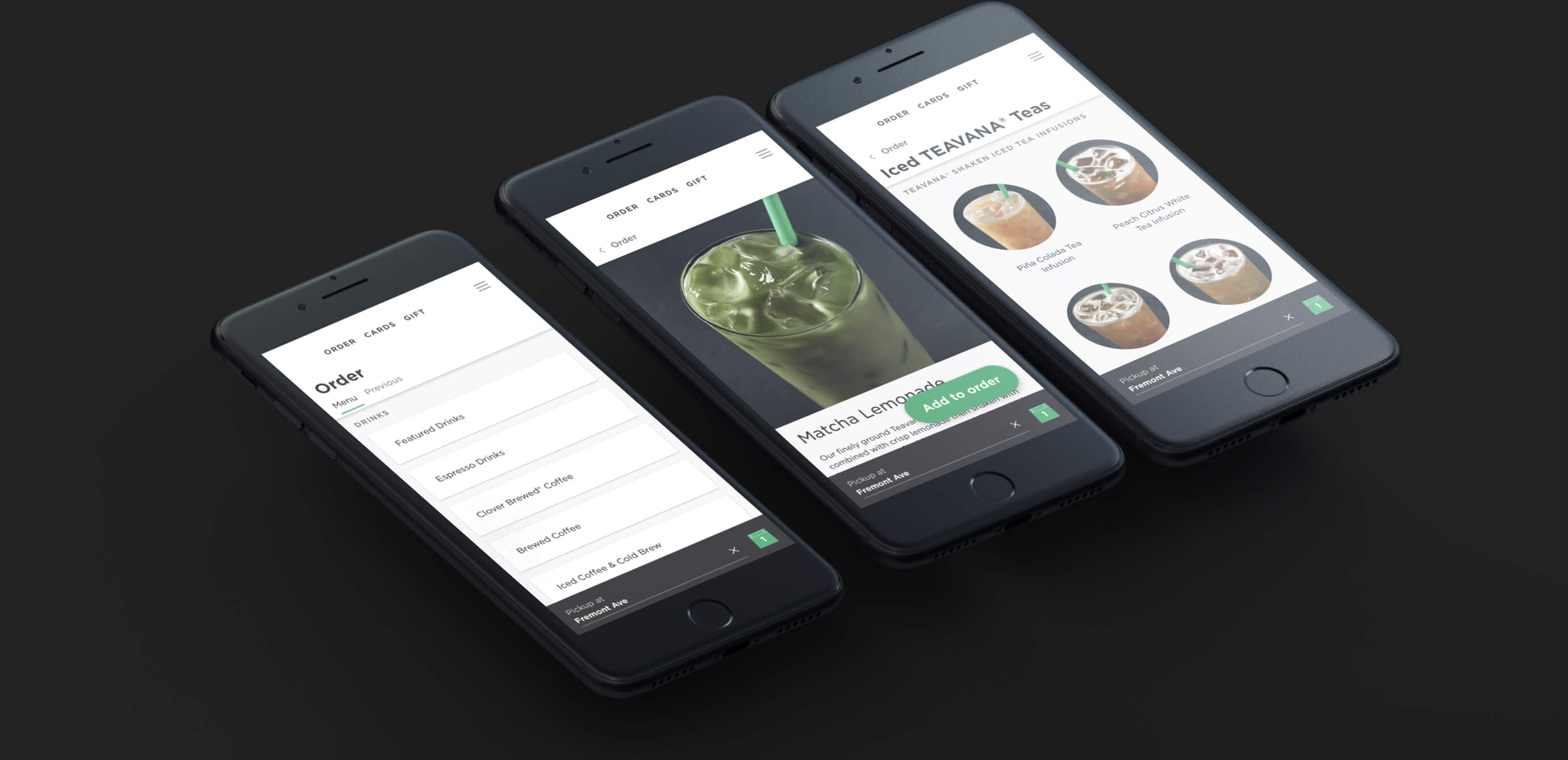
Thanks to modern web technologies like HTML5, Progressive Web Apps (PWA) run in a browser, don't require separate distribution, combine features of native apps with the benefits of a mobile experience and let you keep them on the Home Screen without the hassle of an app store.
In this tutorial, we'll help you install Progressive Web App to your iPhone or iPad Home Screen.
How to clear website data on Apple Watch
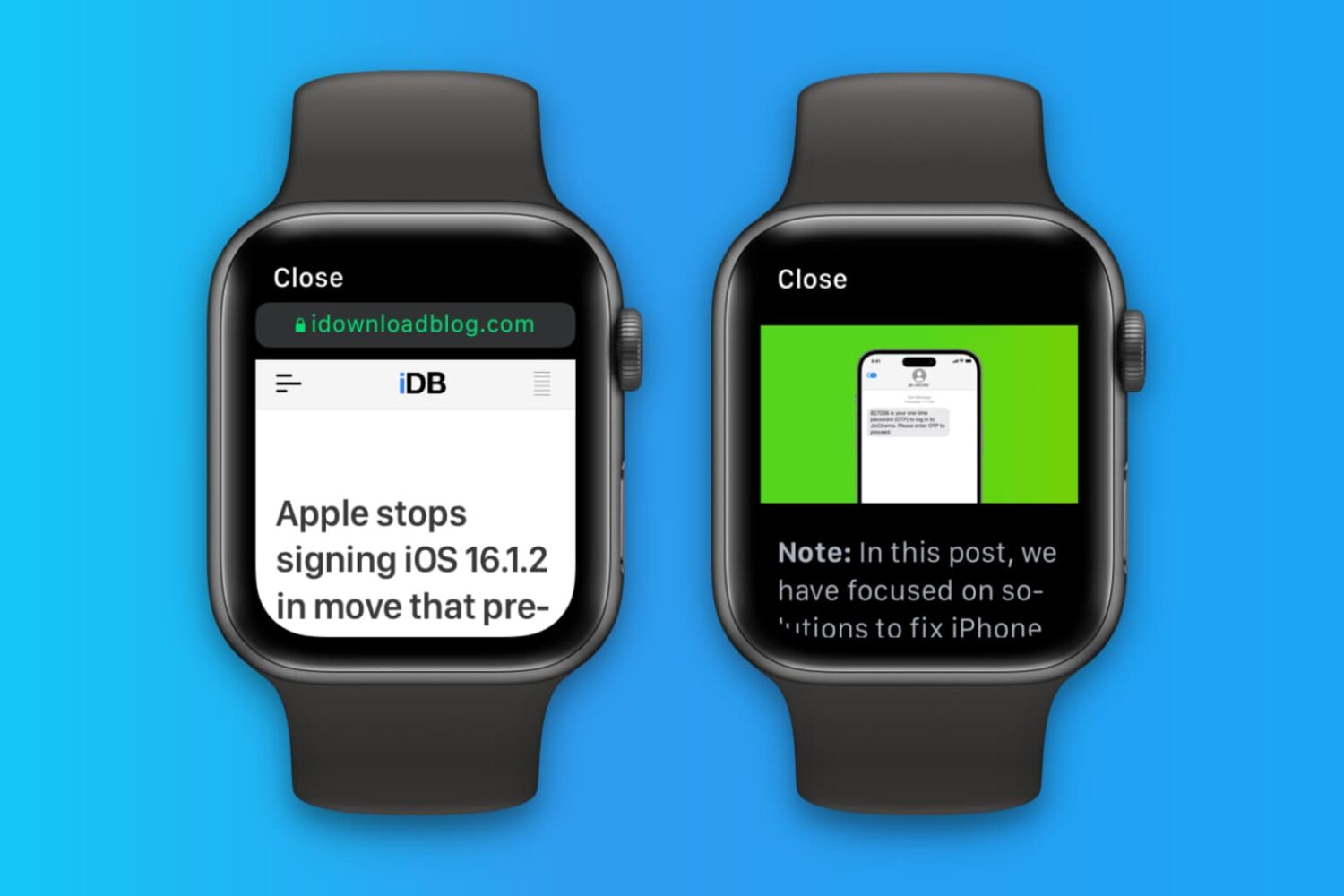
Apple Watch doesn't have its own Safari browser, but limited WebKit engine integration in watchOS lets you open website links embedded in messages and email. Over time, website data may accumulate, and you should clear it to keep things snappy on your Apple Watch.
Your Mac may get some sort of system-wide Dark Mode with macOS 10.14
Apple may be working to expand its Dark Mode-like feature for macOS.
Like iOS 11, iOS 12 will support iPhone 5s

iOS 12 is not expected to phase out older hardware such as iPhone 5s.
Apple shares tips on how to optimize websites for iPhone X using new WebKit API
The iPhone X's new Super Retina display looks pretty stunning. Users have started to note how some websites don't work exceptionally well on the edge-to-edge display because of the notch, and the Home indicator. Apple has now shared some tools for developers that will be coming soon to help them optimize their websites.
Safari 10.1.1 for Mac fixes yet another instance of address bar spoofing
Safari 10.1.1, pushed out as part of today's minor macOS Sierra 10.12.5 software update, fixes yet another instance of address bar spoofing. This is good news because the browser can now protect you from phishing attacks that would typically attempt to fool you into believing you were visiting a genuine website rather than a maliciously crafted webpage.
According to the company's security document, the software fixes a flaw where visiting a malicious website may lead to address bar spoofing. “An inconsistent user interface issue was addressed with improved state management,” states Apple.
Even folks who are extremely mindful of phishing are susceptible to address bar spoofing.
The sophistication of today's phishing attacks came to light when Chinese security researcher Xudong Zheng demonstrated how easily users could be fooled into visiting a fake website that seemingly shows the correct URL in the address bar.
To protect yourself from such attacks in the future, manually type in the URL of the website you want to visit or choose your favorite website from Safari's Bookmarks menu. Of course, you should avoid clicking any suspicious links in an email message, even if they appear to originate from a contact you personally know.
The patched vulnerability was discovered in Safari for macOS, not for iOS.
Apple credits Zhiyang Zeng and Yuyang Zhou of Tencent Security Platform Department with the discovery of the vulnerability CVE-2017-2500 and Zhiyang Zeng of Tencent Security Platform Department with the discovery of the vulnerability CVE-2017-2511.
Moreover, Safari 10.1.1 fixed an issue in Safari's history menu that could lead to an application denial of service after visiting a maliciously crafted webpage. The issue was addressed through improved memory handling.
Lastly, Safari 10.1.1 also includes patches for as many as seven vulnerabilities that were discovered in the WebKit rendering engine, five of which dealing with universal cross site scripting, while fixing an issue with WebKit's Web Inspector where an app could execute unsigned code.
Safari 10.1.1 is available for OS X Yosemite 10.10.5, OS X El Capitan 10.11.6 and macOS Sierra 10.12.5. Apple also released a minor update to iTunes for Mac and Windows today.
iTunes 12.6.1 contains unspecified app and performance improvements and a fix for a WebKit exploit on Windows 7 and later which could result in arbitrary code execution after processing maliciously crafted web content.
Safari update brings fixes for WebKit security flaws on Yosemite, Mavericks and Mountain Lion
Apple has released a considerably important update for Safari on OS X Yosemite, Mavericks and Mountain Lion, patching a WebKit security hole that left users vulnerable.