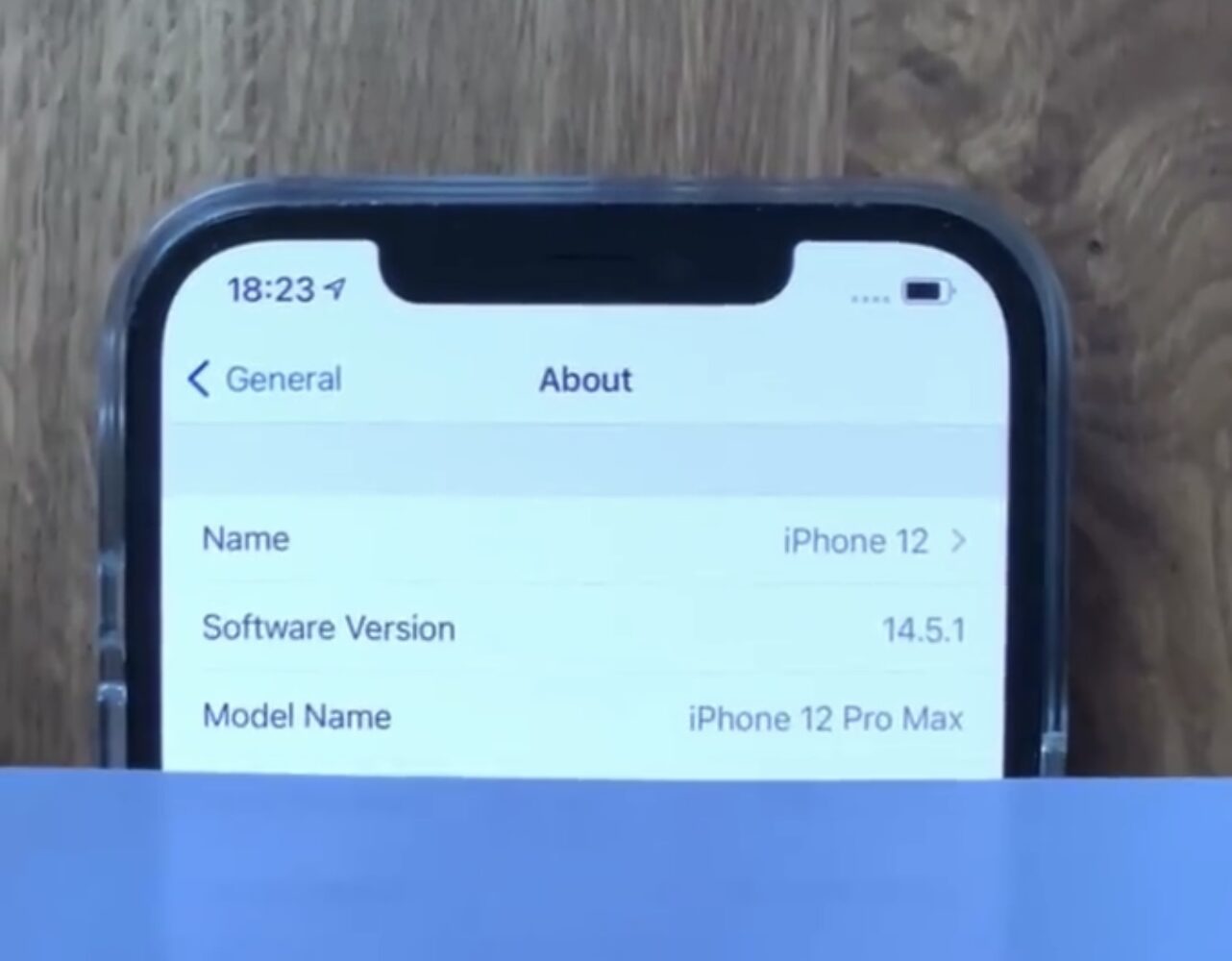
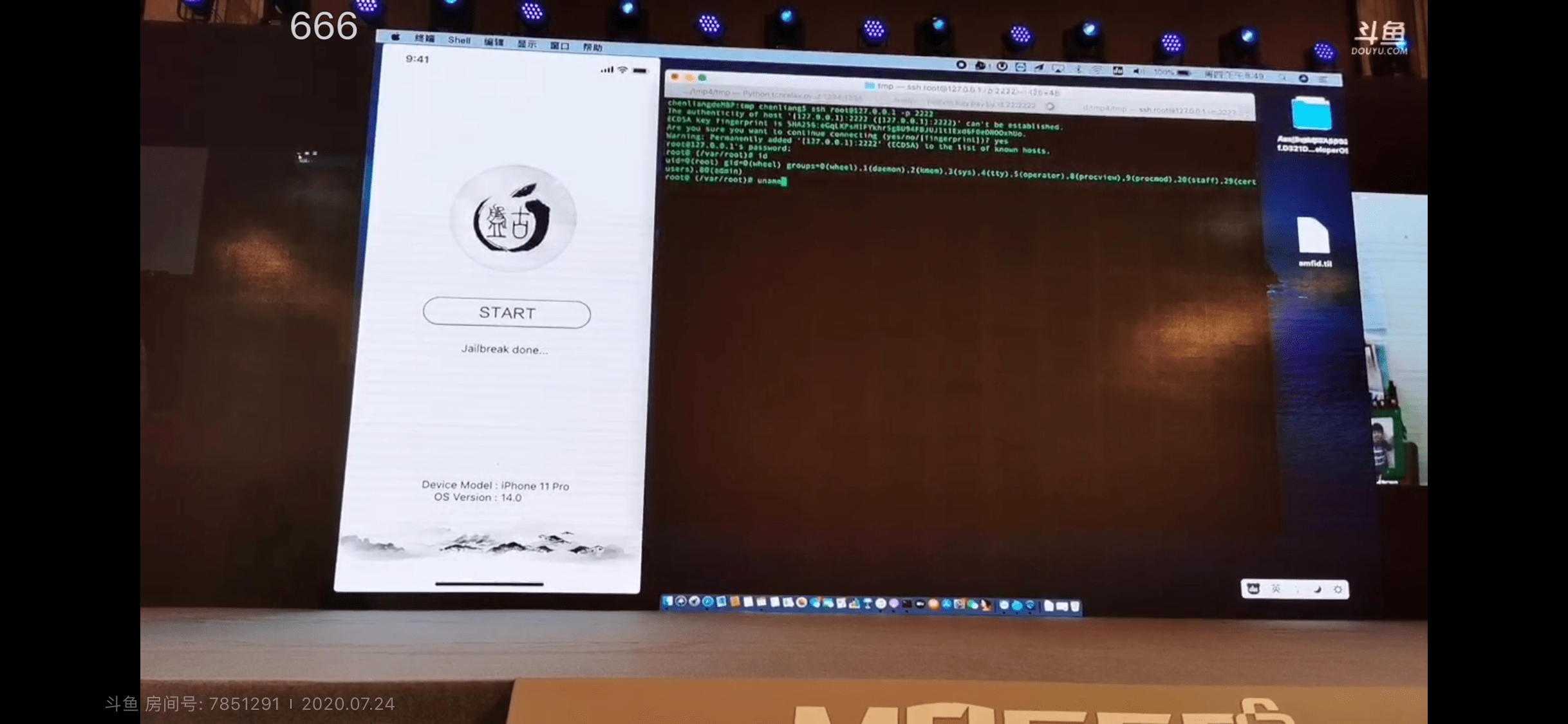
It’s officially Sunday October 24th, and as many avid jailbreakers-at-heart have been waiting for, security researcher Linus Henze has made good on a promise to release an untether that supports up to and including iOS & iPadOS 14.5.1 right out of the box despite a minor postponement this week that was intended to resolve a few bugs prior to releasing.
Linus Henze releases long-awaited untether supporting iOS 14.5.1 and lower out of the box