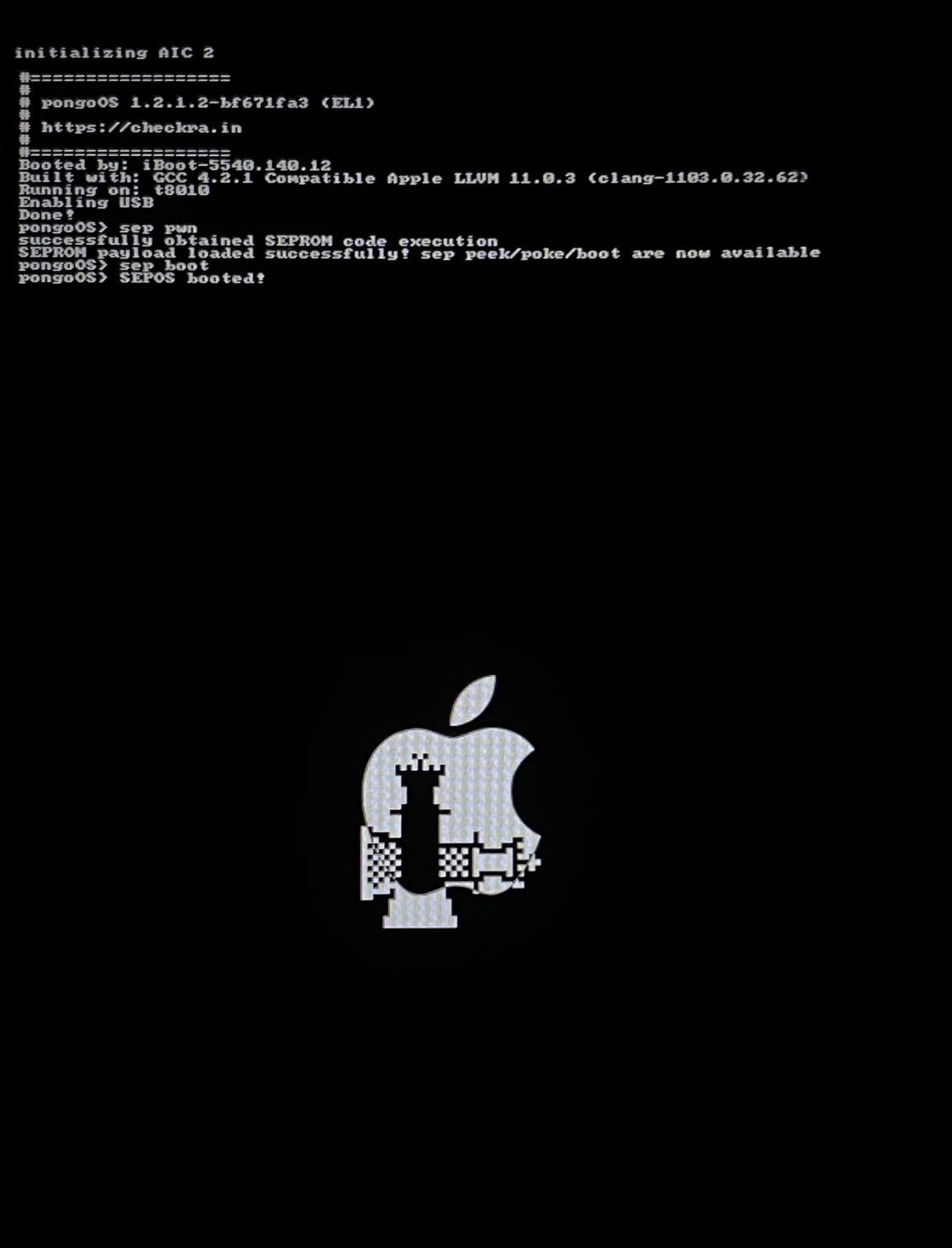
Nearing the end of last month, the Pangu Team took the stage at MOSEC 2020 to discuss a plethora of interesting topics, one of which really stood out from the rest. We’re of course talking about the unpatchable hardware based SEPROM vulnerability that targets a device’s secure enclave processor (SEP).
It wasn’t long after the SEPROM vulnerability was discovered and notes about it were published that famous hackers like Luca Todesco of the checkra1n team began tinkering with it. In fact, it was only yesterday that Todesco Tweeted some particularly eye-catching photos of checkra1n integration on an iOS device and of a T2-equipped Mac running the vulnerability as shown by the Touch Bar’s OLED display: