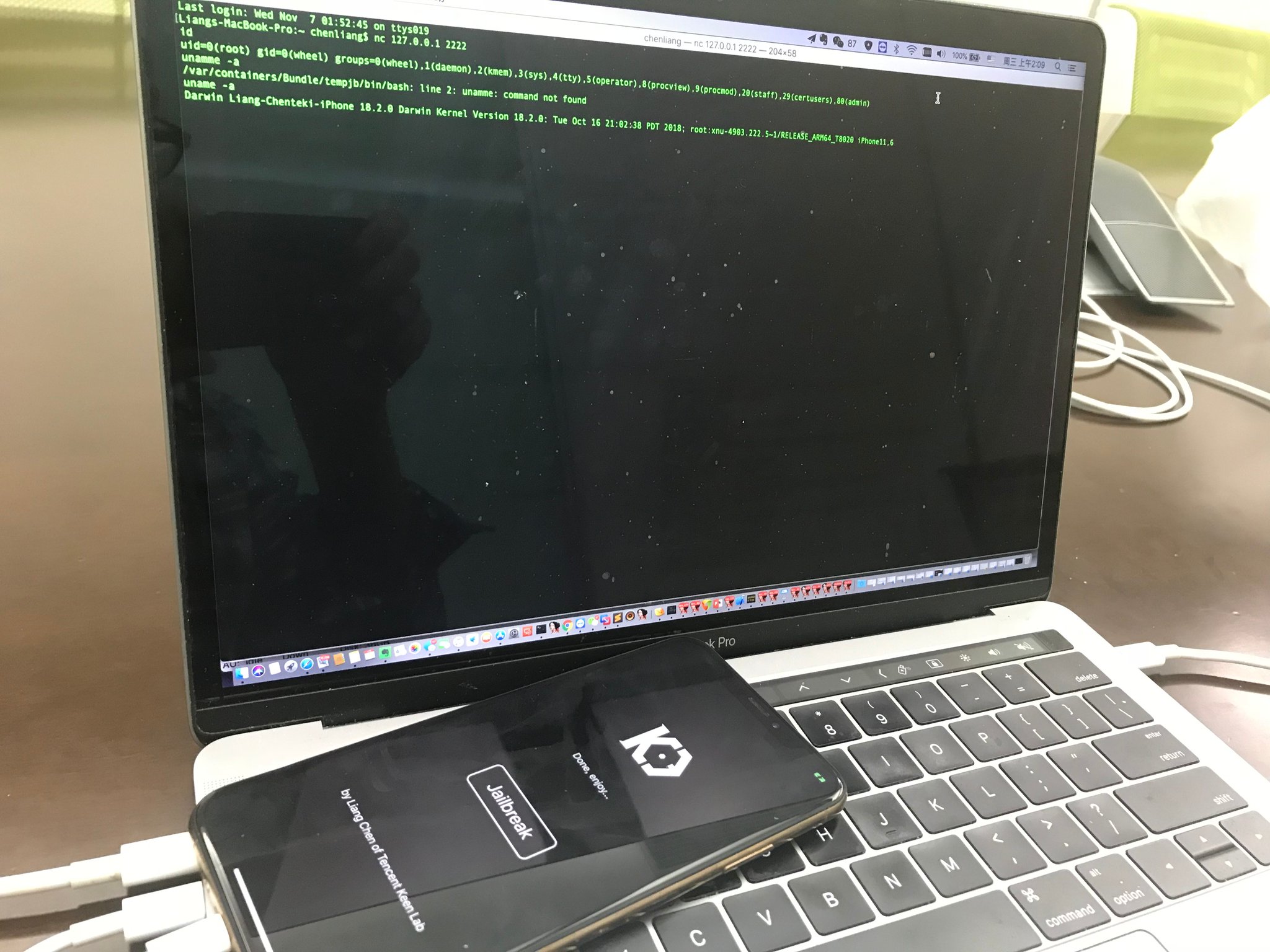
There was no shortage of exciting jailbreak-centric news this past week, but perhaps the most captivating tidbit of all was the announcement that tihmstar was tinkering with an exploit that could hack a subset of devices running iOS 11.2.6-11.4.1 – specifically those with headphone jacks.
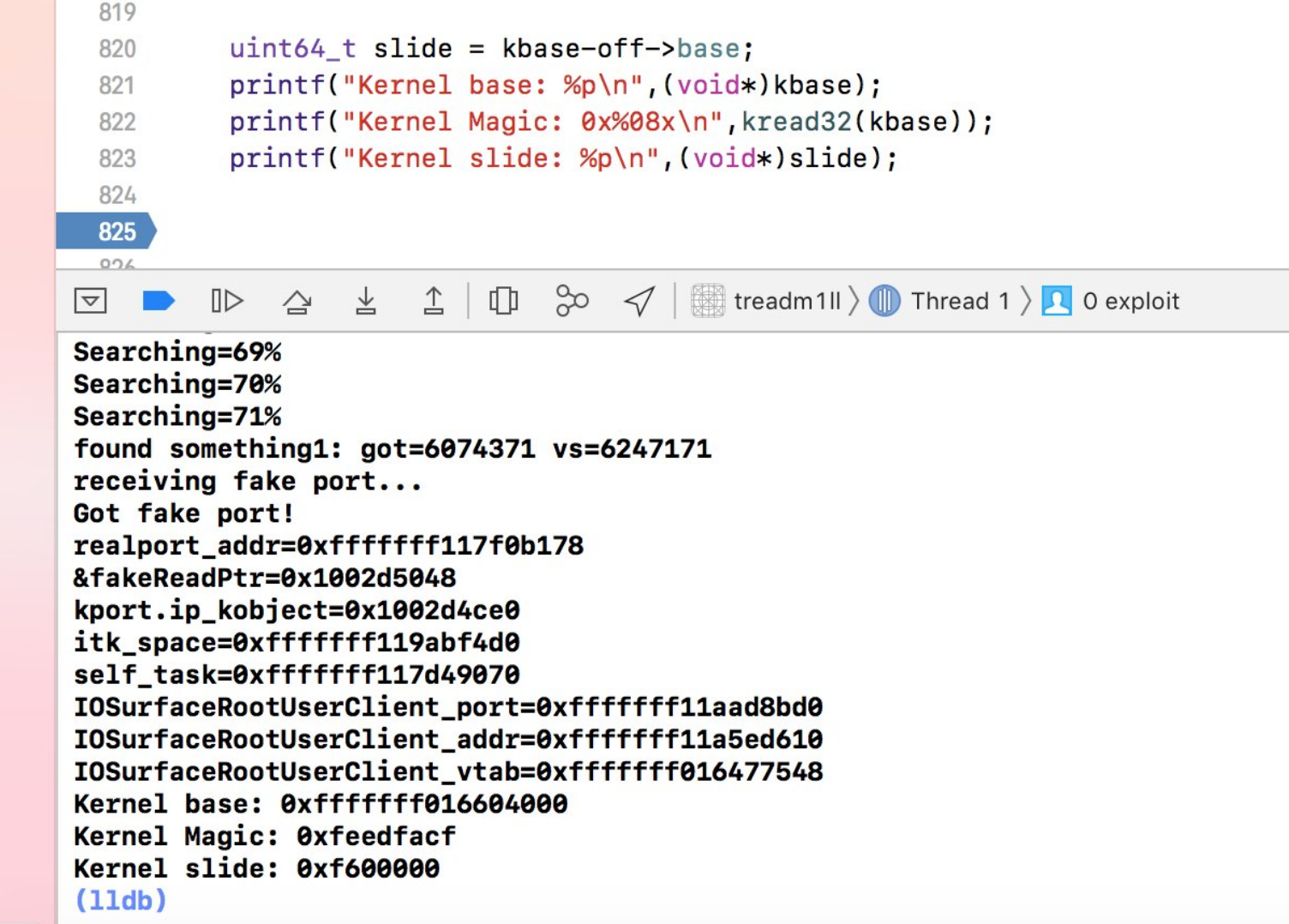
It didn’t take long after the initial announcement for tihmstar to share that he had achieved tpf0, which permits arbitrary reads and writes to a device’s kernel memory. On the other hand, a pair of Tweets shared just weekend shed new light on the hacker’s intentions involving said exploit: