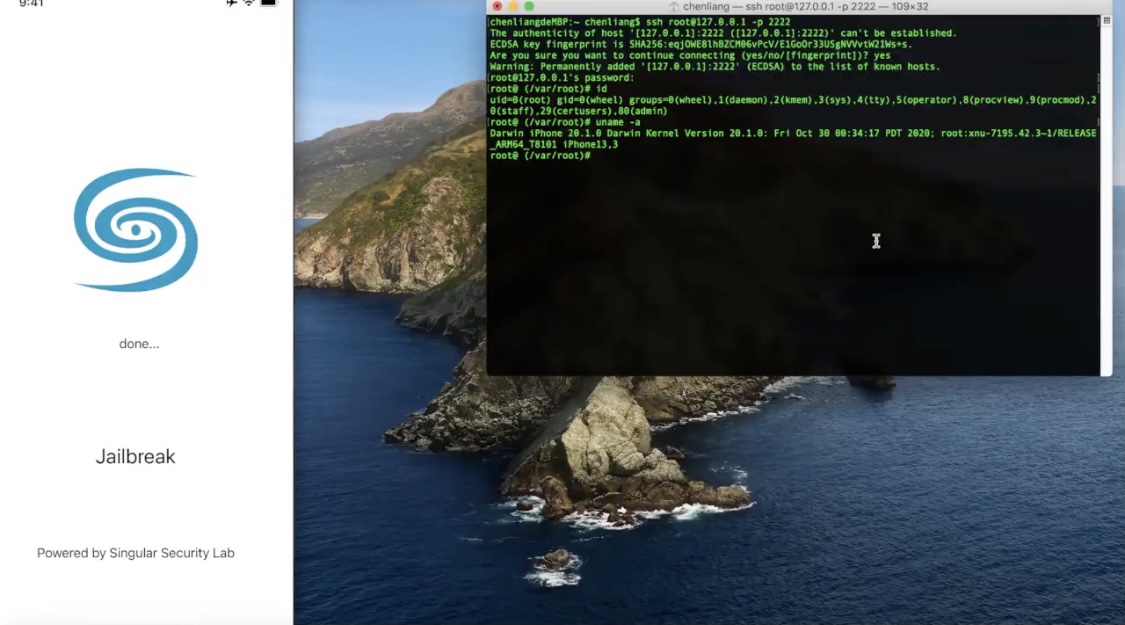
Earlier this year, iOS developer XsF1re garnered a substantial amount of attention from the jailbreak community after releasing the FlyJB kernel-level jailbreak detection bypassafter releasing the FlyJB kernel-level jailbreak detection bypass — a tool that was basically meant to amount to a way for jailbreakers to go undetected by App Store apps that would traditionally bar access to those with pwned handsets.
Soon after, XsF1re pulled the project, citing a loss of confidence, but later reinstated it as FlyJB X upon developing improvements to make the bypass more reliable. Still, it wasn’t without its shortcomings. Over the weekend, however, iOS developer Ichitaso updated his own kernel-level jailbreak detection bypass dubbed KernBypass (unofficial) to version 0.0.5, and from what we can gather, it just might be slightly superior.