The Pangu Team is a name you might remember if you’ve been jailbreaking iPhones and iPads since ye olde days of iOS 9. Despite not releasing a public jailbreak since then, the Pangu Team continues to be hands-on with respect to iOS-related security research.
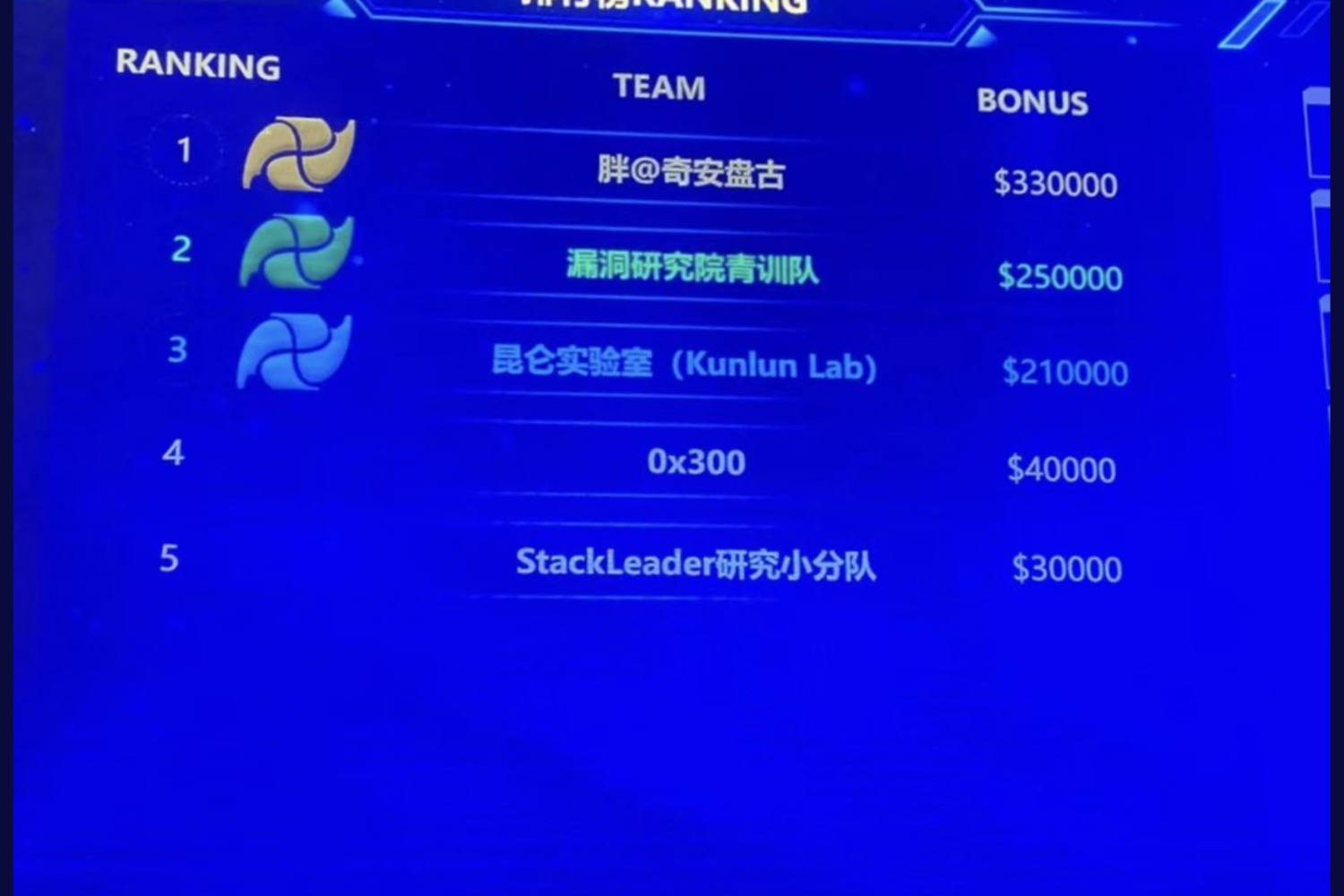
A wonderful example of that happened just this weekend in Chengdu, China at the TianfuCup (TFC) 2021, where the Pangu Team appears to be taking home the first-place prize in the contest by successfully pwning Apple’s brand-new iPhone 13 Pro running iOS 15 via a remote jailbreak. The earnings? A juicy $330,000 cash prize.